Following best practices for media destruction would have prevented compromises to data security faced by Morgan Stanley. What do Morgan Stanley, hospitals, and healthcare organizations across the U.S. and the Kanagawa Prefectural Government of Japan have in common? They all recently faced the same IT Asset Disposition (ITAD) nightmare: data breaches caused by their outsourced data disposition service provider. High-ranking executives from these organizations have endured the public humiliation of having to tell thousands of their patients and customers that their private data is in the hands of thieves, leaving their patient/customers open to financial loss and identity theft; and the executives and their companies open to liability, class-action lawsuits and even criminal charges.
Who gets the Blame?
Many executives and IT professionals mistakenly believe that using an outsourced data vendor protects them from risk and liability. But there is no statute of limitations or safe harbor for improperly discarded IT assets. Partially destroyed data is a ticking timebomb. Improper #ITAD is a risk carried forward indefinitely.
Increasingly, CEOs are caught in the crosshairs. Since 2014, top leaders at Equifax, Target, and Sony, have either resigned or been fired in the wake of prominent cyber incidents according to a recent Wall Street Journal article. As a result, Congress is considering legislation that would impose heavy fines and even prison time on high-level executives who fail to protect corporate data.
An equally dangerous mistake often made by executives and IT professionals is blind trust in the security policies and procedures of their chosen outsourced vendor. Even if IT is vigilant when they initially hand over their data or drives, in time oversight weakens, and mistakes occur.
Data Wiping is not Complete Elimination
Look what happened to Morgan Stanley when they did not implement best practices for media destruction. When Morgan Stanley closed two data centers in 2016, the company decommissioned its computer equipment through an outsourced data wiping (overwriting) vendor. Morgan Stanley expected a complete overwriting of its customer privacy data. This year, they learned they didn’t get what they expected. Instead, data remained on the “wiped” drives, which violated customer privacy. Morgan Stanley now faces significant risks, liability, and lawsuits.
Such was also the case with outsourcing data services vendor Blackbaud. Their data breach impacted 760,000 employees, donors, and patients at Northshore University Health System, Northwestern Memorial Healthcare, Children’s Minnesota, and Allina Health hospitals and clinics.
Knowledge is Power
Forewarned is forearmed. For a comprehensive and effective data security plan that protects your organization from initial acquisition to end of life, you need best practices for media destruction that cover employee behavior, organizational processes, and implementation.
First, protect your chain of custody. Chain of custody and audit trails require no gap in knowledge and handing from initial data/device acquisition to ultimate decommissioning and end of life. Common touchpoints that must be protected include installation, troubleshooting, upgrades, device replacement, and data decommissioning.
Second, have a written set of policies and procedures that every employee who is handling confidential data reads, understands, and signs.
Third, close the loop on data destruction. Too many organizations have a major risk with data and devices at end of life. Make sure you protect both ends of your data security loop by making your data destruction practices as strong as your entry point of attack defenses.
Below is Garner’s recommended best practice steps for magnetic and solid-state media data destruction.
.jpg?width=1024&height=576&name=infographic-1024x576%20(1).jpg)
Magnetic Media
- Ensure no data leaves your facility without first being degaussed.
- Verify and document the degaussing process with an IRONCLAD verification system.
- Use a sticker or physically destroy hard drives to indicate it has gone through the sanitization process.
- Verify and document the degaussing process with a proven erasure verification software.
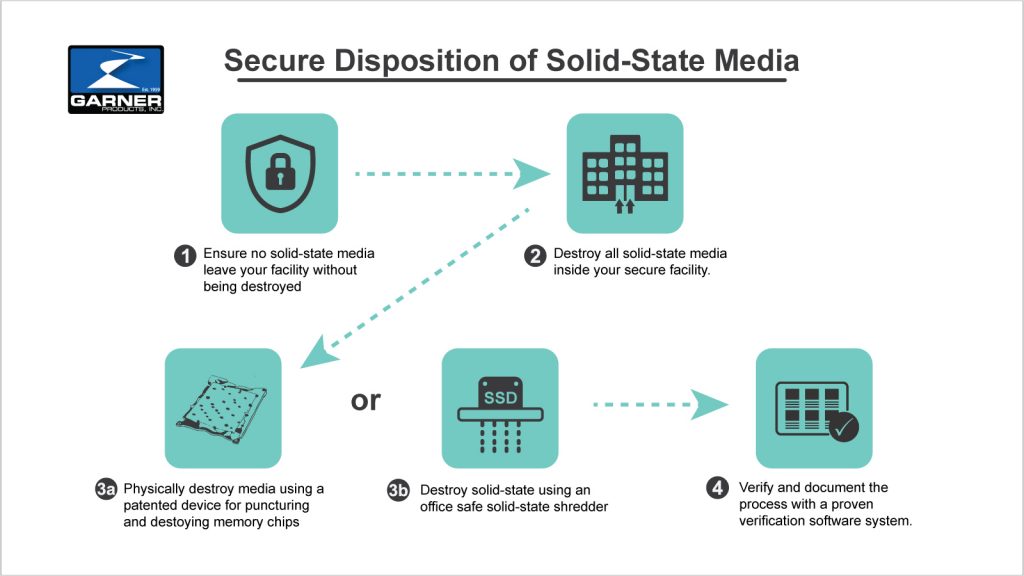
Solid-State Media
- Physically destroy the media while it is inside your secure facility.
- Verify and document the destruction process with an IRONCLAD verification system.
Once these steps have been taken, the media can be safely removed from your secure facility.
Implementing these best practices would have prevented hefty consequences faced by Morgan Stanley, major health care organizations, and the Japanese government breach. To learn how Garner can help you develop data destruction best practices for your organization, visit us online.


LEAVE A REPLY