This is a two-part look at one of the most commonly misunderstood means of data disposal – hard drive overwriting. Today, in Part 1 we’ll look at the general misconceptions. Next week in Part 2 we’ll focus on the dangers of attempting to use overwriting to dispose of top secret, highly confidential data.
It was a scavenger hunt like none other when CNA reporter Jason Godfrey began his mission to discover what really happens to old, discarded cell phones and data drives. What he learned wasn’t pretty. The dangers with overwriting become clear when companies that believed their data had been securely disposed of, learn the opposite was true.
Jason’s documentary, The Trash Trail, discovered passport details and even blueprints from a marine engineering company on hard drives that had been reformatted and declared ‘clean’, before being re-sold to consumers.
The moral of this story – data overwriting isn’t what it promises to be. Many companies believe, and vendors will tell you, that overwriting is quick and easy, it is eco-friendly, it is a safe and secure way to erase data on your hard drives. Overwriting does not secure your data, it creates data insecurity.
Some vendors still believe and will tell you it is completely secure for top secret data disposal, although as of June 2007, the Defense Security Service (DSS) no longer approves of any overwriting procedures “for sanitization or downgrading of Information Systems (IS) storage devices used for classified processing.”
They won’t mentions the dangers of overwriting…

#1: Overwriting is not secure. Not even close.
- First, is the element of choice. One of the biggest problems with overwriting is the ability of the operator to choose to not overwrite all information on the hard drive, virtually guaranteeing your security is compromised.
- Second, the drive must be 100% functioning for the data to be erased. If the drive is worn out or has bad sectors in it, the data cannot be overwritten.
- Every disk drive is different, so the overwriting process that worked for one drive may not work for another.
#2: Overwriting is not fast or easy.
It takes between 8 to 14 hours of continuous writing to overwrite a hard drive that is in good condition. Hard drives that are older or worn out simply fail, leaving unwritten data on the drive. Plus, it usually takes multiple passes – three is recommended — to erase the drive, but operators often take only one pass, leaving you vulnerable to data breach. This takes technical skill and expertise. You must match the overwriting software to the specific OS, BIOS and software of the drive.
#3: Overwriting is not eco-friendly.
Consider that it takes about four hours to overwrite or Secure Erase a 1TB drive; about 900 times the electricity and 240+ times the amount of time that it takes to do an NSA-level degauss. Verification takes that long again, that much incremental electricity, and you still don’t know what happened to any bad sectors: you just hope there was no data there.
#4: Outsourcing drives for overwriting is the least secure choice you can make.
An inherent conflict of interest exists if you are outsourcing your data overwriting process. You want the best security and the outsourcer wants the lowest costs. Using processes like a less thorough overwrite (1 pass vs 3 passes); only overwriting portions of the hard drive, and/or leaving the operating system intact are ways for the vendor to cut expenses and increase the sale price of your used hard drive. If your overwriting software/service is online, you have to expose the drive to the internet to access it. This is a major security violation.
Danger #5: How do you know that your overwriting process has been successful? You don’t!
Because overwriting is done by the hard drive itself, the results can vary dramatically among different hard drives. There is no third party or laboratory check to ensure the drive is working adequately enough to record a pattern over the existing data, leaving you vulnerable and without documentation of destruction.
Unfortunately, too many companies are falling prey to the belief that overwriting is secure. In a recent survey of 1,850 senior leaders from the world’s largest enterprises in APAC, Europe and North America, 36 percent reported using insecure data wiping methods such as reformatting or overwriting when decommissioning hard drives–with no audit trail to protect them.
Erase Your Past to Secure Your Future
As we’ve shown here, overwriting breeds data insecurity. It simply doesn’t offer the level of security organizations that are handling sensitive data need. Degaussers completely destroy data and eliminate the insecurity.
Degaussing is the solution for total data elimination and doesn’t rely on the software or operator to decide what data is sensitive, they erase all data to the highest security level and only takes seconds to complete. This process is laboratory tested and proved.
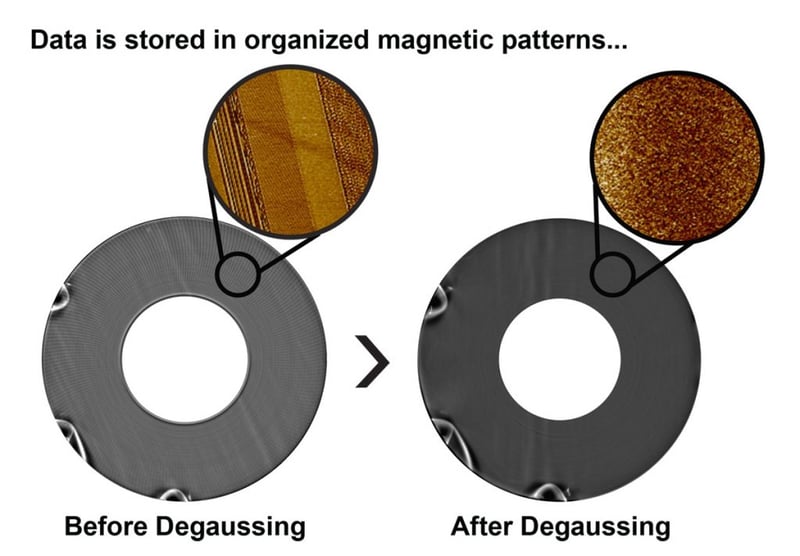
Degaussers Erase all Data on Hard Drives
Unlike overwriting, degaussing erases all data on working and non-working drives up to NSA CSS Evaluated Products Lists standards for TOP SECRET data. Within seconds they deliver a magnetic pulse which encompasses the entire hard drive instantly and permanently removes all data from the disk platters.
In Part 2 of Data Insecurity: The Dangers of Overwriting, we’ll debunk the claim that overwriting meets DoD standards for data sanitation.
Garner Products is a nationally recognized leading manufacturer of NSA/CSS EPL-Listed data destruction equipment offering a full line of degaussers and destroyers for office-quiet desktop units for data elimination.
Learn more about Garner Products at https://garnerproducts.com/


LEAVE A REPLY