Data security stands as a paramount concern in today’s digital landscape, demanding effective data sanitization methods. If you have been relying on wiping, also known as overwriting, or shredding your Data Bearing Devices (DBD), it is crucial to understand the capabilities of forensic data recovery and why even small shred particles of DBD can expose you to risks.
Reminder: The data collector is held accountable for the protection of any Personal Identifiable Information (PII) forever.
Forensic data recovery utilizes specialized techniques and tools to retrieve information from DBD, including hard disk drives (HDD), solid-state drives (SSD), and other media. These techniques can recover data presumed to have been deleted, overwritten, or destroyed.
For the purpose of this blog, let's focus on hard disk drives, which are still among the most commonly used DBD. HDDs store data on platters by magnetically encoding binary codes (1’s and 0’s) on the platters’ surface. The HDDs’ read/write heads detect these magnetic patterns and convert them into readable data displayed on your screen. When the HDD is no longer needed, common methods of decommissioning the HDD and securing its content from unauthorized access are encryption, overwriting, shredding, and degaussing.

The Power of Forensic Data Recovery
Advancements in forensic technology enable experts to recover data from encrypted, overwritten, or shredded segments of a hard drive. Forensic data recovery utilizes a variety of methods and technologies to extract and reconstruct data from storage media. These methods may include:
- Physical Imaging: This involves creating a bit-by-bit copy of the storage device, including all data, deleted files, and even hidden partitions. Physical imaging ensures that the original evidence remains intact while allowing forensic analysts to work with a duplicate copy for investigation.
- File Carving: File carving is a technique used to extract files and fragments of data from unallocated space or damaged sectors of a storage device. By analyzing the underlying file structures and metadata, forensic experts can identify and reconstruct files even if their directory entries have been deleted or corrupted.
- Decryption: In cases where data is encrypted to protect it from unauthorized access, forensic specialists may employ decryption techniques to recover the original information. This can involve brute-force attacks, cryptographic analysis, or leveraging encryption keys obtained through legal means.
- Fragmentation Analysis: When files are fragmented across multiple sectors on a storage device, forensic tools can analyze the file system to reconstruct the complete file by piecing together its fragments. This process enables experts to retrieve valuable information even from fragmented or partially overwritten files.
- Steganography Detection: Steganography is the practice of concealing data within other files or media to avoid detection. Forensic data recovery experts use specialized tools and algorithms to detect and extract hidden information from images, audio files, or other digital content.
Success in data recovery depends on factors like the type of storage device, extent of damage, and method of data protection used. Because of these variables, the advancements in forensic technology and data recovery capabilities underscore the need for thorough data sanitization to ensure that sensitive data cannot be recovered or exploited by malicious actors.
The Risk of Small Shred Particles
With physical data destruction, like shredding a hard drive, the size of shred particles matters. Smaller particles make data recovery harder, but even they pose risks because shredding doesn't remove the data. Small shred particles still contain information that, in the wrong hands and with the right equipment, can be retrieved.

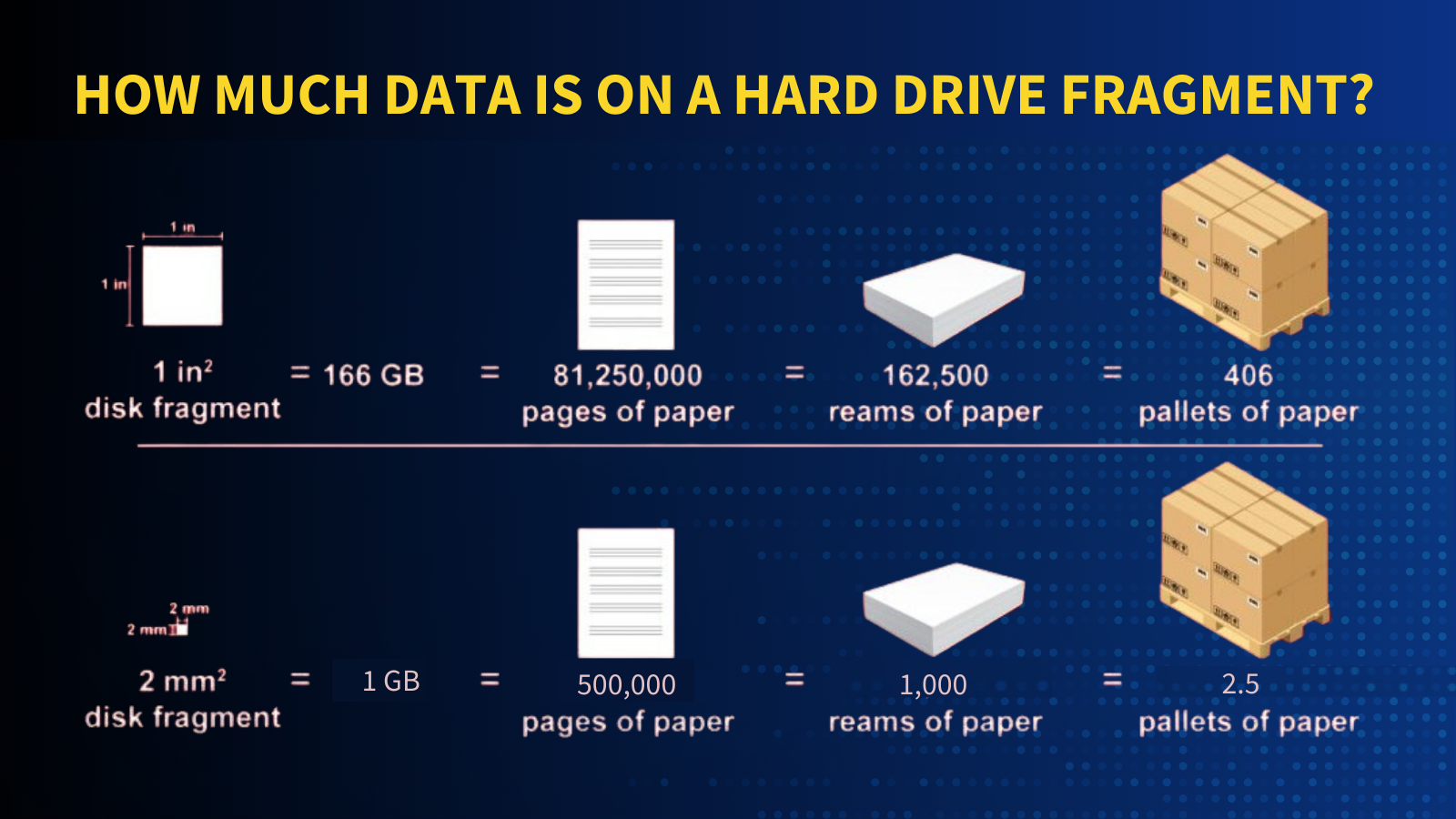
The National Security Administration (NSA) recognizes the very real threat of forensically recovering data off shred particles. In fact, to meet the NSA HDD shred standards requires the use of a disintegrator that generates particles that measure no larger than 2 mm, the size of pencil lead. See NSA/CSS Policy Manual 9-12.
But even a 2mm² disk fragment still contains retrievable data. A 2 mm² disk fragment is the paper equivalent of 2.5 pallets of paper, which is 1,000 reams of paper. Advanced forensic techniques continually improve, potentially enabling data recovery from smaller particles. Although the extracted information may not constitute a full data set, it highlights the persistence of data remnants even in the aftermath of physical destruction and exposes a significant risk if sensitive data is not properly sanitized before device disposal.
A study titled "Data Recovery in a Case of Fire-Damaged Hard Disk Drives and Solid-State Drives" delves into successful data recovery from shredded hard disk drives and solid-state drives damaged by fire. This highlights the evolving landscape of digital forensic research, as discussed in the article "Digital Forensic Research: Current State of the Art" and the paper "Next-Generation Digital Forensics: Challenges and Future Paradigms." While these studies showcase advancements in data recovery, they also underscore the importance of robust data destruction measures to effectively counter potential forensic investigations.
Recommended Read: Why is shredding not a secure data destruction method?
Degaussing: The Preferred Method for Data Sanitization
Degaussing emerges as a remarkably effective solution to the challenges posed by forensic data recovery. In the context of HDDs where data is magnetically encoded, a degausser comes into play by generating a magnetic field. This magnetic field neutralizes the stored magnetic data patterns on the HDD, ensuring complete and verifiable data destruction. Notably, unlike shredding and overwriting, degaussing an HDD with a degausser of appropriate strength provides 100% destruction of data on HDDs. After degaussing, the data no longer exists. The media is now safe for recycling or disposal.

Compared to physical destruction methods such as shredding or overwriting, the degaussing process excels in terms of reliability. As discussed above, shredding a hard drive, although it complicates data access, does not eliminate the data. Similarly, wiping or overwriting data still retains the potential for recovery. While it overwrites existing data, the underlying data remains susceptible to recovery. Moreover, overwriting cannot address non-functioning sectors of the drive. The overwriting process will fail to overwrite any damaged parts of the drive, leaving your data vulnerable to potential data breaches.
Recommended Read: The Dangers of Overwriting Part I
Recommended Read: What is degaussing? Secure data destruction explained.
Recommended Read: How to select the right degausser? A comprehensive guide.
Degaussing: The Preferred Method for Data Sanitization
Incorporating degaussing into your comprehensive data security strategy offers substantial benefits. It goes beyond assuring complete data destruction, playing a pivotal role in safeguarding sensitive information from unauthorized access or misuse. Degaussing facilitates compliance with stringent data protection regulations that mandate thorough sanitization of storage media within your controlled facility before disposal. Known for its unparalleled effectiveness, degaussing becomes a cornerstone in ensuring that you and your business navigate secure data disposal with confidence and strict adherence to regulatory standards.
In a landscape where a potential data breach carries severe consequences such as hefty fines, legal complications, financial losses, reputational damage, operational disruptions, and erosion of customer trust, leaving data disposal to chance is not an option. Ensure complete hard disk data destruction by employing secure data destruction methods like degaussing, providing a robust defense against potential data recovery threats.

Conclusion
In essence, the complexities of forensic data recovery and the risks associated with small shred particles highlight the critical need for comprehensive data destruction methods. Because physical destruction alone is not foolproof, the implementation of degaussing emerges as a powerful solution. As organizations face the ever-present threat of data breaches and their severe consequences, the proactive adoption of a complete data destruction method like degaussing becomes imperative. It not only fortifies organizations against potential data recovery threats but also instills confidence in navigating the challenges of the digital era with unwavering security and regulatory adherence.
Speak to one of our Masters of Destruction to learn more about how Garner Products’ degaussers can align with your evolving Data Bearing Devices’ destruction needs.
About Garner Products
Garner Products designs and manufactures premium equipment that delivers complete, permanent, and verifiable data destruction. For over 60 years, Garner has provided the education, systems, and support that enable customers worldwide in all industries to securely destroy data.


LEAVE A REPLY