The New Zero Trust Reality
Nothing. Nil. Zero. That’s how much trust you should have in your users, devices, and network when it comes to today’s increasingly dispersed and complex data environment, according to the National Security Agency (NSA). While much of the focus of “Zero Trust” is on front-end IT, these best practices also apply to end-of-life media.
Bold cybercriminals can no longer be kept at the perimeter of the network. They can now easily penetrate and prowl uncontested throughout your network. Once inside, they target the weakest links and simply log in using stolen or otherwise compromised credentials.
Your only effective defense is the implementation of a Zero Trust security model.
In developing your Zero Trust Model, you must address the three key principles recommended by the NSA guidelines. Adopt a Zero Trust mindset. This mindset assumes all network traffic is malicious and that all devices and infrastructure may be compromised. It calls for rapid damage assessment, control, and recovery operations.
Embrace Zero Trust guiding principles
These principles start with never trust, always verify. Treat every user, device, application/workload, and data flow as untrusted; assume and operate as though a breach has already occurred; explicitly verify all resources consistently and securely using multiple attributes (dynamic and static) to derive confidence levels for contextual access decisions to resources.
Leverage Zero Trust design concepts
Define mission outcomes; architect from the inside-out; determine who/what needs access to the DAAS to create access control policies; inspect and log all traffic before acting.
The Zero Trust Model is based on the assumption that no person or entity is to be trusted until verified. So, why would companies setting up Zero Trust models for their networks and data still use third-party disposal vendors at end of life?
The perils of third-party data disposal are well known
Just ask corporate giant Morgan Stanley. The investment banker was fined $60M when their third-party disposal company left confidential data on drives thought to be “wiped” clean.
Read Michael Harstrick’s article Old Data. New Liability.
Trusting a third-party data disposal vendor compromises every other aspect of your Zero Trust protection
It leaves you vulnerable to breaches, lawsuits, and hefty agency fines. It can and has led to job loss at the C-suite level. Since 2014, top leaders at Equifax, Target, and Sony, have either resigned or been fired in the wake of prominent cyber incidents.
The only valid Zero Trust practice for end-of-life data disposal is to degauss, destroy and verify in-house.
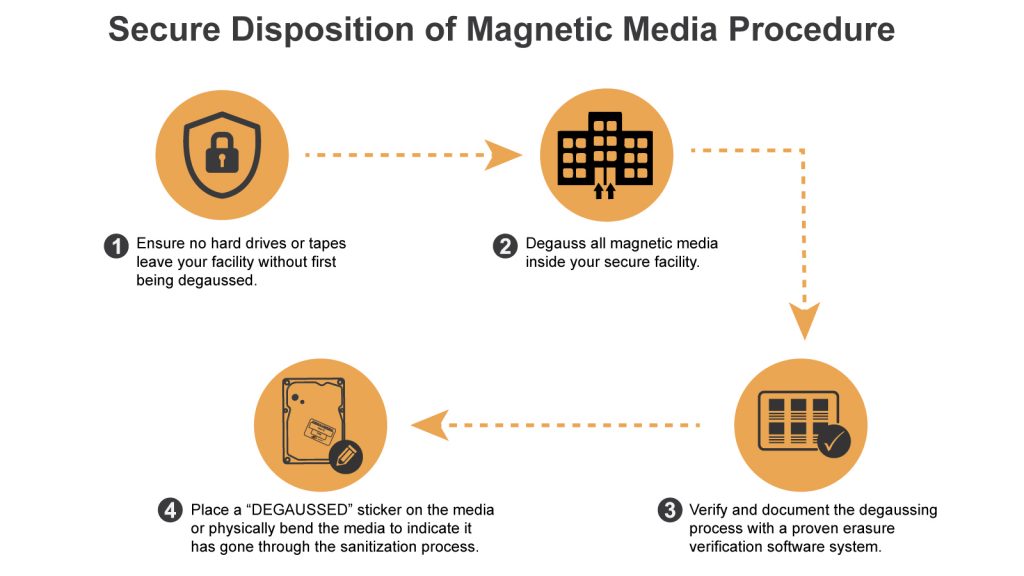
- Ensure no hard drives or tapes leave your facility without first being degaussed.
- Sanitize all media in-house at the source of the data to maintain chain of custody.
- Degauss and destroy the media and devices to eliminate the risk of a data breach from employee theft or misuse.
- Verify your data sanitization process with a system that captures and keeps a record of the destruction. Garner offers our IRONCLAD Erasure Verification System to capture JPG images of degaussed media and to automatically generate a certificate of erasure and destruction.
Garner Products is the internationally recognized, leading manufacturer of NSA/CSS EPL-Listed data erasure and destruction equipment. Garner offers a full line of hard drive degaussers and destroyers, from office-quiet desktop units to equipment for Top Secret data elimination. Learn more about Garner Products at GarnerProducts.com


LEAVE A REPLY